Ruta de navegación
Blogs
Entries with Categories Global Affairs Security and defence .
[Edgar A. Porter & Ran Yin Porter, Japanese Reflections on World War II and the American Occupation. Amsterdam University Press. Amsterdam, 2017. 256 p.]
REVIEW / Rut Natalie Noboa Garcia
 World War II has provided much inspiration for an entire genre of literature. However, few works fail to capture Asian perspectives on the beginning, development, end, and consequences of World War II. Additionally, the attitude and outlooks of defeated parties are often left out of popularized discussions of conflicts. Because of these two factors, Japanese perspectives during the war and occupation have often served as only minor discussions in World War II literary work.
World War II has provided much inspiration for an entire genre of literature. However, few works fail to capture Asian perspectives on the beginning, development, end, and consequences of World War II. Additionally, the attitude and outlooks of defeated parties are often left out of popularized discussions of conflicts. Because of these two factors, Japanese perspectives during the war and occupation have often served as only minor discussions in World War II literary work.
This sets the stage for Edgar A. Porter and Rin Ying Porter's Japanese Reflections on World War II and the American Occupation, which presents the experiences of ordinary Japanese citizens during the period. The book specifically focuses on the rural Oita prefecture, located on the eastern coast of the island of Kyushu, a crucial yet critically unacknowledged place in Japan's role in World War II. Hosting the Imperial Japanese Navy base that served as the headquarters for the Pearl Harbor attack, being the hometown of the two Japanese representatives that signed the terms of surrender at the USS Battleship Missouri, serving as the place for the final kamikaze attack against the United States, and providing much of Japan's foot soldiers for the conflict, Oita is ripe with unchronicled, raw, and diverse accounts of the Japanese experience.
The collective stories of the 43 interviewees, who lived through the war and occupation present the varied perspectives of soldiers, sailors, and pilots, who are often at the centre of war discussions and experiences, but also that of students, teachers, nurses, factory workers and more, providing a multidimensional portrayal of the period.
The book begins with the early militarization of the Oita prefecture, specifically in Saiki, the location for one of the most crucial instructions for the Japanese Imperial Navy. This first chapter features the perspectives of young Saiki citizens raised during the period who still see the Pearl Harbor attack with a conflicted yet enduring pride, setting the stage for following interesting discussions on Japanese post-war sentiment.
Another important aspect addressed by the Porters in this work is the mass censorship and indoctrination that took place in Japan during the war period. During this time, average censorship and military-based education helped to obscure the actual happenings of the conflict, particularly in its earlier years, as well as rallying the population in support for the Japanese navy. As well as presenting censored portrayals of the war itself, local Oita editorials both highlighted and encouraged public support for the war and the glorification of death and martyrdom. This indoctrination is also acknowledged by the Porters in relation to traditional Japanese Shinto beliefs on the emperor, specifically his divine origins. Japan's average portrayals of the conflict concerning the state and emperor as well as its moral education curriculum feed into each other, applying moral pressure to the support of war efforts.
Japanese Reflections on World War II and the American Occupation also provides particularly interesting insights on East Asian regionalism, particularly from the perspective of Imperial Japan, which viewed itself as an "older brother leading the newly emerging members of the Asian family towards development" and promoted the idea that the Japanese were racially superior to other Asian ethnic groups. The first-hand accounts of many of the atrocities committed by Japanese in cities such as Nanjing and Shanghai as well as their glorification by the Japanese press add to the book's depth and relevance.
As the war approached an end, conflict reached Oita. The targeting of civilians and the bombing of factories during American air raids lowered Oita morale. Continued air raids on Oita City, the prefecture's capital city, rapidly fueled the region's fear and resentment towards American soldiers.
In conclusion, Japanese Reflections on World War II and the American Occupation manages to present important first-hand accounts of Japanese life during one of the most consequential moments in modern history. The impact of these events on current Japan is particularly interesting when it comes to Japanese culture, especially when it comes to the glorification of war in Japanese education as well as the rising tide of Japanese nationalism.
[Myra MacDonald, Defeat is an Orphan. How Pakistan Lost the Great South Asia War. Penguin. London, 2016. 313 p.]
review / Ramón Barba
 One might think that Myra McDonald's book rather confuses the reader, as degree scroll talks about a Great War in the Indian subcontinent of which there is no record. In reality, the book financial aid helps the reader - especially the Western reader, who is more distant from the cultural and historical framework of that part of the world - to understand the complexity of the relations between India and Pakistan. A Reuters correspondent for more than thirty years, with long experience in the region, McDonald knows how to add up data concrete facts, without getting bogged down in anecdote, and quickly get to the underlying force behind them.
One might think that Myra McDonald's book rather confuses the reader, as degree scroll talks about a Great War in the Indian subcontinent of which there is no record. In reality, the book financial aid helps the reader - especially the Western reader, who is more distant from the cultural and historical framework of that part of the world - to understand the complexity of the relations between India and Pakistan. A Reuters correspondent for more than thirty years, with long experience in the region, McDonald knows how to add up data concrete facts, without getting bogged down in anecdote, and quickly get to the underlying force behind them.
Her thesis is that since the birth of the two states with the partition of the Jewel in the Crown at the break-up of the British Empire, Pakistanis and Indians have been engaged in a long confrontation, which has even had its moments of live fire. It has been a prolonged and bitter enmity between the two countries, with its sporadic battles: a Great War, according to the author, which Pakistan ultimately lost.
Generally, while India has sought its national affirmation in the exercise of democracy, Pakistan has based its national idiosyncrasies on Islam and conflict with India, with the dispute over control of Kashmir its bloodiest manifestation. This fixation with India, from agreement with McDonald, has led Islamabad to use support for jihadist groups to create instability on the other side of the partition line, plunging Pakistan itself into an abyss from which it has so far been unable to extricate itself. McDonald follows a generally objective argument, but the book seems to be written from India, with little sympathy for the Pakistanis.
The story begins with the episode of the hijacking of the Indian Airlines plane between Christmas Eve and New Year's Eve 1999 by five Kashmiri guerrillas, with 155 people on board, which led to a serious conflict between Islamabad and New Delhi, as the Indian government interpreted that the operation had received some backing from the neighbouring country. The episode serves to describe the dramatic standards of the strategic struggle between the two countries, which the previous year culminated their development of the atomic bomb.
The book pays particular attention to this degree program to achieve the nuclear weapon - the Indians because the Chinese had it, the Pakistanis because they saw the Indians catching up - and which raised a question core topic of nuclear proliferation: can weapons be used on a smaller scale between two deadly enemies when both have the atomic bomb? It has been shown to be so, and not only that, McDonald argues: Pakistan's lack of fear of an Indian nuclear attack, given that it is deterred by Pakistan's own arsenal, would have made Islamabad more confident in encouraging terrorist attacks against India.
In the early 1960s the status in India was somewhat delicate: in 1964 China had detonated the atomic bomb, which, coupled with Pakistani pressure in Kashmir, put the world's largest democracy at a difficult juncture. This led to India's launch of the Smiling Buddha in 1974 (as an unloaded bomb) and the beginning of close competition with Pakistan to join the small nuclear club, as a consequence of the dialectical logic that then governed their relationship. Although it was believed that the bomb might be in one side's possession, it was not until the late 1998 detonations that this became clear.
The author considers that the two countries arrived that year on a very even footing: India, which was larger, had to resolve small internal crises in order to move forward, while Pakistan enjoyed a certain stability. However, the achievement of the atomic bomb meant that Pakistan, after a misreading of reality, failed to take advantage of its opportunities in the era of globalisation that was then opening up, and remained stuck in a bellicose logic, while India made the leap that has made it gain undoubted weight as a world power. This is the Pakistani "defeat" of which degree scroll speaks.
In addition to this attention to more recent decades, the text also looks back to 1947, when the two independent states were born, to explain many of the dynamics of the subsequent relationship between the two. Relations with China, Pakistan's ally, and with the United States, which had closer interests with Pakistan and is now closer to India, are also discussed.
In its ten operational years the "Dome" has shown effectiveness, but a comprehensive political regional solution is needed
In 2011 Israel deployed its "Iron Dome" mobile defense system in response to the rocket attacks it suffered the previous years from Lebanon (Hezbollah) and Gaza (Hamas). The Israel Defense Force claims that the system has shown an 85% - 90% success rate. However, it offers mixed results when other considerations are taken into account. Its temporary mitigation of the menaces of the rocket attacks could distract Israelis in seeking out a comprehensive political regional solution; possibly a solution that could make systems like the "Iron Dome" unnecessary.
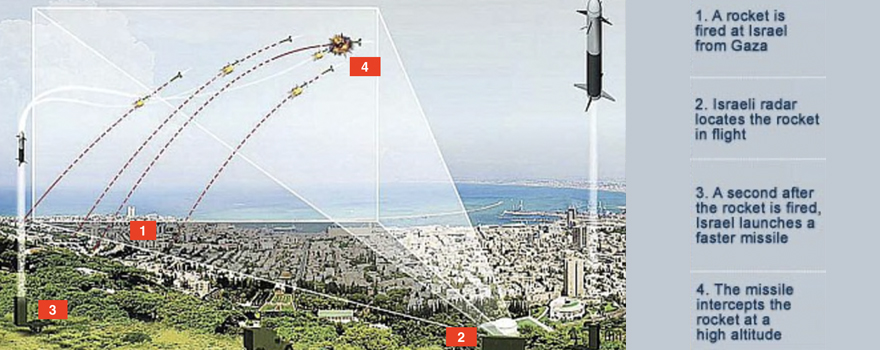
▲ How "Iron Dome" works; explanation on an image produced by Rafael Advanced Defense Systems
ARTICLE / Ann M. Callahan
The "Iron Dome" is a mobile defense system developed by Rafael Advanced Defense Systems and Israel Aerospace Industries developed, produced and fielded in 2011 to respond to the security threat posed by the bombings of rockets and projectiles shot into Israel, many of which landed in heavily populated areas.
Bombings into Israel intensified during the 2006 Second Lebanon War when Hezbollahfired approximately 4,000 rockets from instructions in the south of Lebanon. From Gaza to the South, an estimated 8,000 projectiles were launched between 2000 and 2008, mostly by Hamas. To counter these threats, the Defense Ministry, in February 2007, decided on the development of the "Dome" to function as a mobile air defense system for Israel. After its period of development and testing, the system was declared operational and fielded in March 2011.
The system is the pivotal lower tier of a triad of systems in Israel's air defence system.
The "David's Sling" system covers the middle layer, while the "Arrow" missile system protects Israel from long-range projectiles.
The Iron Dome functions by detecting, analyzing and intercepting varieties of targets such as mortars, rockets, and artillery. It has all-weather capabilities and is able to function night or day and in all conditions, including fog, rain, dust storms and low clouds. It is capable to launch a variety of interceptor missiles.
Israel is protected by 10 "Iron Dome" batteries, functioning to protect the country's infrastructure and citizens. Each battery is able to defend up to 60 square miles. They are strategically placed around Israel's cities in order to intercept projectiles headed towards these populated areas. Implementing artificial intelligence technology, the "Dome" system is able to discriminate whether the incoming threats will land in a populated or in an uninhabited area, ignoring them in the latter case, consequently reducing the cost of operation and keeping unnecessary defensive launches to a minimum. However, if the "Dome" determines that the rocket is projected to land in an inhabited area, the interceptor is fired towards the rocket.
A radar steers the missile until the target is acquired with an infrared sensor. The interceptor must be quickly maneuverable because it must intercept rudimentary rockets that are little more than a pipe with fins welded onto it, which makes them liable to follow unpredictable courses. It can be assumed that the launchers of the rockets know as little as the Israelis as to where the rockets would end up landing.
Effectiveness
The IDF (Israel Defense Force) claims an 85% - 90% success rate for the "Iron Dome" in intercepting incoming projectiles. Operational in March 2011, to date the "Iron Dome" has successfully destroyed approximately 1,500 rockets. The destruction of these incoming rockets has saved Israeli lives offering physical protection and shielding property and other assets. In addition, for the Israelis it serves as a psychological safeguard and comfort for the Israeli people.
Regarding the "Dome" as an asset for Israel's National Security Strategy, while standing as an undeniable asset, it has had mixed results regarding its four major pillars of Deterrence, Early, Active Defense and Decisive Victory as well as some unintended challenges.
For instance, regarding the perspective of its psychological protection for the Israeli people, it is thought to also effect Israeli public in a negative manner. Regardless of the fact that it currently offers effective protection to the existing threats it could, in fact, help cause a long-term security issue for Israel. Its temporary mitigation of the menaces of the rocket attacks could distract Israelis in seeking out a comprehensive political regional solution; possibly a solution that could make systems like the "Iron Dome" unnecessary.
In addition, while the "Dome" suffices for now, it cannot be expected to continue this way forever. Despite the system's effectiveness, it is just a matter of time before the militants develop tactics or acquire the technology to overcome it. The time needed in order to accomplish this can be predicted to be significantly reduced taking into account the strong support from the militant's allies and the considerable funding they receive.
Still a comprehensive diplomatic solution is needed
Today, the world's militaries of both state and non-state actors are engaged in a technological arms race. As is clearly known, Israel's technological dominance is indisputable. Nevertheless, it, by no means, stands as a guarantee as destructive technology becomes more accessible and less expensive. As new technologies become more available they are subject to replication, imitation and increased affordability. As technologies develop and are implemented in operations, counter techniques can shift and new tactics can be developed, which is what the militias are only bound to do. Moreover, with the heavy funding available to the militias from their wealthy allies, acquiring more advanced technologies becomes more likely. This is a significant disadvantage for Israel. In order to preserve their upper hand, constant innovation and adaptation is a necessity.
The confusion between the short-term military advantage the technology of the "Dome" offers and the long-term necessity for a comprehensive and original political, diplomatic solution is seen as a risk for Israel. Indeed, Amir Peretz, a minister in Israel's cabinet, told the Washington Post in 2014 that the "Iron Dome" stands as nothing more than a "stopgap measure" and that "in the end, the only thing that will bring true quite is a diplomatic solution".
Despite these drawbacks, however, in all the positive aspects that the system offers clearly outweighs the negative. The "Iron Dome" stands undeniably as a critical and outstanding military asset to Israel's National Security, even while Israel works to address and mitigate some of the unforeseen challenges related to the system.
![Qasem Soleimani receives a decoration from Iranian Supreme Leader Ali Khamenei in early 2019 [Khamenei's Office] Qasem Soleimani receives a decoration from Iranian Supreme Leader Ali Khamenei in early 2019 [Khamenei's Office]](/documents/10174/16849987/tension-oriente-medio-blog.jpg)
▲ Qasem Soleimani receives a decoration from Iranian Supreme Leader Ali Khamenei in early 2019 [Khamenei's Office]
COMMENT* / Salvador Sánchez Tapia
The death in Iraq of General Qasem Soleimani, head of the Iranian Quds force, at the hands of a US drone is one more link in the process of growing deterioration of the already bad relations between the United States and Iran, the latest chapter of which has been experienced since 2018, the year in which President Trump decided to break the so-called "agreement (JCPOA) signed with Iran in 2015 by the Obama administration and the other members of the G5+1.
The attack on Soleimani, carried out in retaliation for the death of a US contractor in an attack apparently launched by the Iraqi Shiite militia Kataib Hezbollah on the US K1 base in Kirkuk on 27 December, has marked a qualitative change in the situation in the country. subject response that the U.S. is accustomed to give to incidents of this kind. subject for, for the first time, the goal It's been a stop manager of the Islamic Republic of Iran.
Immediately after the assassination, during the funeral for the deceased general, Ali Khamenei, Iran's supreme leader, announced in somewhat apocalyptic terms that the attack would not go unanswered, and that it would come directly from Iranian hands, not through proxies. It came, in fact, on the night of January 8 in the form of a massive missile attack on two instructions U.S. military personnel stationed in western Iraq and Iraqi Kurdistan. Contradicting Iranian statements that the bombings had killed some 80 Americans, the U.S. administration was quick to assert that there had been no casualties. leave because of the attacks.
In the aftermath of this new attack, the world held its breath waiting for an escalation by Washington. However, President Trump's statements on January 8 seemed to defuse tensions by arguing that the absence of U.S. casualties was indicative of an Iranian attempt to de-escalate. The U.S. will not respond militarily, although it has announced its intention to tighten the economic sanctions regime until the country changes its attitude. With this, the risk of an open war in the region seems averted, at least momentarily.
Are we affected by the tension between the United States and Iran?
Obviously, yes, and in several ways. First of all, we cannot ignore the fact that several European countries, including Spain, maintain significant military contingents deployed in the region, operating within the framework of NATO, the United Nations and the European Union in missions such as "Inherent Resolve" in Iraq, "Resolute Support" in Afghanistan, UNIFIL in Lebanon, "Active Fence" in Turkey, etc. or "Atalanta" in the Horn of Africa.
In the cases of Iraq and Afghanistan in particular, the Spanish troops deployed in the aforementioned missions work closely partnership with other NATO allies, including the United States. Although in principle Spanish soldiers – or, for that matter, those of the other NATO nations – are not in the crosshairs of Iranian responses, specifically directed against North America and its interests, there is no doubt that any attack by Iran on American units could collaterally affect the contingents of other nations operating with them. if only for a matter of mere geographical proximity.
Less likely is that Iran would attempt a response against any non-U.S. contingent through one of its proxies in the region. This would be the case, for example, of Hezbollah in Lebanon, a country in which Spain maintains a significant contingent whose security could be affected if it group, either on its own initiative, or at the behest of Iran, attempts to attack any UNIFIL unit or facility. This option, as we say, is considered unlikely because of the negative impact it would have on the international community in general, and because of the proximity to Israel of the deployment of UNIFIL.
The escalation has led to an increase in the alert level and a reinforcement of U.S. troops in the region. If the increase in tension were to continue, it would not be out of the question that Washington could come to some sort of agreement. subject It could appeal to the support of its partners and allies, either with troops or resources. It is difficult to determine at what time and under what conditions such a situation might occur application, for what purpose and, very importantly, what response Europe would give to it, taking into account the concern with which the Old Continent observes an escalation in which it is not interested, and the state of relative coldness that relations between the United States and Europe are going through.
As a result of the assassination, Iran has made public its intention to dissociate itself completely from the provisions of the agreement that I was still watching. In other words, he says he feels free to continue his nuclear program. Undoubtedly, this last nail in the coffin of the JCPOA may lead to an open degree program nuclear power in the region with negative consequences for regional security, but also for European security. The rise of the issue From our point of view, the collapse of nuclear powers is, in itself and from our point of view, bad news.
Finally, and as a side effect of the escalation, the price of a barrel of oil is beginning to show a disturbing upward trend. If there are no corrective measures by increasing production from other countries, the trend could continue. There is no need to dwell on what the increase in the price of oil means for the economy. Economics and, of course, for the national one.
Russia and China in the crisis
Russia is making efforts to replace the United States as the leading power in the region and to present North America as a leading power. partner unreliable, which abandons its allies in difficulty. The escalation of the crisis could have a negative impact on this effort, delaying it or, in the worst case, ending it if, in the end, the United States were to reverse its policy of gradual derailing withdrawal in the Middle East due to an increase in tension with Iran. Russian rhetoric will be anti-Washington. In the end, however, it will do nothing to increase the tension between the United States and Iran, and it will, probably, keep it within a tolerable level or decrease.
Russia is not so much a staunch ally of Iran as one of convenience. Iran is a competitor of Russia for influence in the region – particularly in Syria – and may seek to negatively influence Islamism in the Russian Federation. On the other hand, Russia is not enthusiastic about the idea of Iran acquiring nuclear weapons.
China's stance is conditioned by its heavy dependence on the steady flow of oil from the Middle East. For this reason, it has no interest in the instability that this increase in tension entails. It is expected to act as an element of moderator, seeking to use the crisis as an opportunity to increase its influence in the region. China is not interested per se in becoming the arbiter of security in the region, but it is interested in a stable, trade-friendly region.
The project "One Belt, One Road" is another reason why China will try to keep the crisis within acceptable limits. The Middle East is an element core topic in the project recreation of a sort of new Silk Road. An open war between the U.S. and Iran could adversely affect the country. project.
In summary, neither Russia nor China are interested in an escalation between the United States and Iran that could lead to an open war between the two nations that would jeopardize oil supplies, in the case of China, and the establishment as the main international power in the region, in the case of Russia. Both will try to temper the Iranian response, even if, at the level of statements, they speak out against the assassination of Soleimani.
* This text extends a previous comment made by the author to El Confidencial Digital.
[Michael E. O'Hanlon, The Senkaku Paradox: Risking Great Power War over Small Stakes. Brookings Institution Press. Washington, 2019. 272 p.]
review / Jimena Puga
 After the end of the Cold War, in which it confronted the Soviet Union bloc by defending the values of the Western order, the United States remained in the world as the hegemonic country. At present, however, it is rivaled by Russia, which despite its weakness Economics it struggles not to lose any more influence on the international stage, and for China, which, although still a regional power, aspires to replace the United States at the pinnacle of the world. The challenge it is not only for Washington, but for the entire West, as its very values are called into question by the advance of the diary of Moscow and Beijing.
After the end of the Cold War, in which it confronted the Soviet Union bloc by defending the values of the Western order, the United States remained in the world as the hegemonic country. At present, however, it is rivaled by Russia, which despite its weakness Economics it struggles not to lose any more influence on the international stage, and for China, which, although still a regional power, aspires to replace the United States at the pinnacle of the world. The challenge it is not only for Washington, but for the entire West, as its very values are called into question by the advance of the diary of Moscow and Beijing.
The West needs to respond firmly, but how far does it need to go? When should you say enough is enough? Are you willing to go to war even if the cumulative steps taken by Russia or China are in themselves relatively minor or occur on the periphery? That's what Michael E. is asking. O'Hanlon, researcher Brookings Institution, in The Senkaku Paradox: Risking Great Power War over Small Stakes. The book addresses a number of possible scenarios in the context of global hegemonic change and competition between the world's major powers for power.
The scenarios put forward by O'Hanlon consist, on the one hand, of a possible annexation of Estonia or Latvia by Russia, without prior consent and through a military attack. And, on the other, China's military conquest of one of the largest islands that make up the Senkaku, the name given by Japan to an archipelago it administers near Taiwan and which Beijing calls Diaoyu. In both cases, it is difficult to assess which side would have a better military strategy or to predict which side would win a hypothetical war. In addition, there are many unknown variables about cyber vulnerabilities, submarine operations, or the accuracy of missile strikes on each country's strategic infrastructure.
Thus, the author wonders whether both the United States and its allies should respond directly with a military offensive, in response to an initial attack, or if they should limit themselves to an asymmetrical response, focused on preventing future attacks, combining such responses with economic retaliation and certain military actions in different scenarios. What is clear is that while remaining vigilant in the face of the possible need to strengthen their positions on the international chessboard, Western countries must remain prudent and provide proportionate responses to possible crises, aware that their values – the defence of freedom, justice and the common good – are the greatest advantages of their democratic systems.
At present, Western democratic systems are under strong populist pressure, although there is nothing to suggest that countries with well-established democracies such as France, Germany or Spain will generate conflicts between them, much less in the European Union, which has been a guarantee of peace and stability since the 1950s. For its part, it would be advisable for the Trump administration to react with greater prudence in certain situations, to avoid an escalation of diplomatic tension that would unnecessarily increase the risks of conflict, at least regionally or economically.
Neither Moscow nor Beijing today poses an immediate threat to U.S. global hegemony, but China is the fastest-growing power in fifty years. Such rapid growth could lead China to dispense with multilateralism and regional cooperation and to carry out regional influence through economic or military imposition. That would make the People's Republic a threat.
Although it is true that the United States has the best military force, it is expected that around the year 2040 there will be both military and economic parity between the Central Empire and the American country. Thus, Europe and the United States, in the face of possible aggression from China – or Russia, despite their state of gradual decline – should respond appropriately and, as the White House says, be "strategically predictable, but operationally unpredictable". And all this is done by seeking allies at the international level and by putting military pressure on the aggressor in regions that are compromised by him.
As the author argues, the White House needs better and more credible options to design an asymmetric defense based on deterrence and containment plans, which have the use of force as an option. For example, the article Article 5 of the North Atlantic Treaty is not the best deterrent weapon for the US and its allies, as it poses a danger to stability and leaves no room for action in the event of deterrence. However, with the new subject NATO member countries would not be obliged to "fire the first bullet", so there would be room for other collateral actions, without the need to resort to direct confrontation to stop a possible escalation of more serious hostilities.
What is clear, O'Hanlon argues, is that both China and Russia seek to challenge the international order by any means necessary. subject and the West must adopt strategies aimed at anticipating possible future scenarios, so that they can be prepared to deal with them with guarantees of success. These measures don't have to be just military. For example, they will have to prepare for a long and painful economic war through defensive and offensive measures, while the US stops imposing tariffs on aluminum and steel on its allies. In addition, the US has to be careful about overusing the economic sanctions applied to financial transactions, especially the prohibition of access to the SWIFT code of the banking communication system, because if not, the countries allied with Washington will end up creating alternatives to SWIFT, which would be a disadvantage and a sample of weakness vis-à-vis Moscow and Beijing.
![Operations in cyberspace can be part of a status of hybrid warfare carried out by state or non-state actors [Pixabay] Operations in cyberspace can be part of a status of hybrid warfare carried out by state or non-state actors [Pixabay]](/documents/10174/16849987/guerra-hibrida-blog.jpg)
▲ Operations in cyberspace can be part of a status of hybrid warfare carried out by state or non-state actors [Pixabay]
essay / Ana Salas Cuevas
The hybrid threat is an all-encompassing term subject coordinated actions to influence the decision-making of States, making use of political, economic, military, civil and information means. These actions can be carried out by both state and non-state actors.
The term "Grey Zone" is used to determine the boundary between peace and war. It is a new tactic that has nothing to do with the real war that pits armies of different states against each other. Hybrid warfare is about achieving results by directly influencing society by demoralizing it. It is undoubtedly an effective tactic and much simpler for the attacking countries, since the investment, both economic and human, is lower than in real war. Resources such as propaganda, manipulation of communications, economic blockades, etc. are used. And in the absence of strong international legislation in relation to these conflicts, many countries consider this conflict to be a serious problem. subject of actions as tolerable.
Introduction: The Hybrid Threat
The term hybrid threat was popularized after the clash between Israel and Hezbollah in 2006 to designate "the integration of unconventional and irregular tactics, techniques, and procedures, mixed with terrorist acts, propaganda, and connections to organized crime."[1]
The goal Essential to the hybrid threat is to achieve results without resorting to actual war, pitting societies and not armies against each other, almost completely crumbling the distinction between combatants and citizens. The goal the military takes a back seat.
The actions carried out within this subject of conflicts focus on the employment from media such as cyberattacks, disinformation, and propaganda. They have as goal the exploitation of economic, political, technological and diplomatic vulnerabilities, breaking communities, national parties, electoral systems and producing a great effect on the energy sector. These performances are not random, they are planned and organized. These attacks are not linear in nature. They can have direct consequences in another area. For example, the drone attack on wells in Saudi Arabia in September 2019 had a direct impact on the Economics global.
Cyberspace has become a novel aspect in this scenario. Thanks in large part to the technological and information revolution, we are now facing a changing world order, in which the information provided by the media is accessible to anyone from anywhere in the world. It is no coincidence, therefore, that the Internet is one of the most important fronts when talking about hybrid warfare. In this area, the rules are not clearly established and States and non-State actors have a greater margin of action in the face of the classical power of States. Fake news, disinformation and opinion-based facts are tools at anyone's fingertips to influence public order.
Through manipulation in these areas, the hybrid enemy manages to considerably weaken one of the most important pillars of the state or community to which its actions are directed: the trust of citizens in its institutions.
Ambiguity is one of the distinguishing characteristics of cyber activity. The hybrid enemy not only exploits the inherent difficulty of the network It is not only a global approach to attributing hostile actions to a particular actor, but rather reinforcing it through the use of hybrid strategies such as synchronization.
Cyberterrorism and hacktivism
As we have just seen, cyberspace is one of the preferred domains of the hybrid enemy. In it, he will frequently resort to cyberthreat, a cross-cutting threat with a very difficult attribution of authorship. This cannot be reliably substantiated in most cases, in which there are only suspicions, making it very difficult to obtain evidence. These cyberthreats could be divided into four blocks that we will proceed to analyze one by one.
First of all, cyber espionage has as its goal the political, economic and military spheres. Numerous states routinely resort to cyber espionage. Among them, some such as China, Russia, Iran or the United States stand out. States can carry out cyberespionage actions directly, using their intelligence services, or through intermediary agents such as companies influenced by those States.
Secondly, cybercrime, in most cases carried out for profit, and whose impact on the Economics global GDP is estimated at 2% of the world's GDP. The main targets of cybercrime are information theft, fraud, money laundering, etc. It is usually carried out by terrorist organizations, organized crime, and hackers.
Thirdly, cyber-terrorism, the main objectives of which are to obtain information and everything else. subject communications to citizens. The main actors, as can be deduced, are terrorist organizations and intelligence agencies.
Cyberterrorism has a series of advantages over conventional terrorism, and that is that it guarantees greater security over anonymity, in addition, there is a greater cost-benefit ratio and in the geographical scope there is a great advantage in terms of delimitation. In Spain, there was a reform of terrorist offences through Organic Law 2/2015, in which articles 571 to 580 of the Penal Code were fully reformed. At the same time, Organic Law 1/2015 also approved the reform of the Penal Code, affecting more than 300 articles[2].
Finally, fourthly, hacktivism, whose main targets are web services, along with the theft and unauthorized publication of information. When hacktivism is used for the benefit of terrorism, it becomes terrorism. The group Islamic terrorist DAESH, for example, uses cyber means to recruit fighters into its ranks. As agents, two groups stand out, the group "Anonymus" and "Luizsec," in addition to the intelligence services themselves.
Cyberterrorism has very specific aims: to subvert the constitutional order, to seriously disrupt social peace and to destroy our model global. This is an emerging threat of leave Probability, but high impact. The main problem with all this is the lack of existing legislation in this regard, but which is gradually emerging; For example, in 2013 the starting point was given with the publication of a communication from the committee of the European Union on security – the "European Union Cybersecurity Strategy"[3] – from which the strategies must be reviewed every 5 years. This is in addition to Regulation 2019/881 of the European Parliament and the committee (EU) of 17 April 2019.
Grey Zone
The concept of the grey area has recently been coined in the field of programs of study to describe the framework of the hybrid enemy's performance. The term describes a state of tension as an alternative to war, operating in a stage of formal peace.
The conflict in the grey zone is centred on civil society. Its cost, therefore, falls directly on the population. In any case, it operates within the limits of international legality. The protagonist is usually a major international state (a power) or a non-state actor of similar influence.
The actions of an enemy operating in the gray zone are aimed at dominating certain "zones" that are of interest to them. The types of responses within what is defined as the grey area will depend on the threat faced by the country in question.
Legal point of view
If we speak from a legal point of view, it is more accurate to use the term hybrid war, only when there is an open and not covert armed conflict.
Indeed, a major problem arises from the difficulty in applying appropriate national or international legislation to hybrid threat actors. Agents involved generally deny hybrid actions and try to escape the legal consequences of their actions by taking advantage of the complexity of the legal system. They act on the edge of the box, operating in unregulated spaces and never exceeding legal thresholds.
Hybrid Threat Responses
The response to the hybrid threat can occur in different areas, not mutually exclusive. In the military sphere, a direct military confrontation can even be conceived, which can be seen as "tolerable" if it avoids confrontation with a great power such as the United States or China. In the same way, these military confrontations are respected because of the defenselessness of the occupied territories in the face of the threat that the occupying State seeks to prevent.
In the economic sphere, the answer makes it possible to impose on an enemy the costs of subject which are sometimes more direct than military responses. In this field, one way to adopt non-provocative defensive measures is through the imposition of immediate and formal economic sanctions on an aggressor.
An example of this is the economic sanctions that the United States imposed against Iran for considering it a nuclear threat. To this end, it is important to highlight the substance of this matter.
In 2015, the Joint Comprehensive Plan of Action (JCPOA) on Iran's nuclear programme was signed, committing Iran to comply with the agreement and the United States to withdraw the economic sanctions imposed. However, in 2018 Trump announced the withdrawal of the agreement and the reinstatement of sanctions. In the course of these events, several countries have spoken out about these unilateral decisions taken by the U.S. government. China and Russia, for their part, have expressed their disagreement, making official statements in favor of Iran.
Iran's case is a clear example of an economic response to the grey zone, where states use this element of power to deny the aggressor's participation in different institutions or agreements and control their zone of influence.
The United States, like many other powers, finds this status of superiority a decisive advantage in conflicts within the grey zone. Because of the importance of the financial and political power of the United States, the rest of the countries, including the European Union, cannot but accept this subject unilateral actions.
Conclusions
By way of conclusion, we can conclude that hybrid activity in the grey zone has important consequences for the society of one or more States as a whole, and produces effects that can have a global reach.
Hybrid threats fundamentally affect civil society, and can have a demoralizing effect that leads to the psychological collapse of a state. The employment This tactic is often referred to as "formal peace." Despite the fact that there is no direct confrontation between armies, this technique is much more effective since the attacking country does not need to invest as much money, time and people as in real war. In addition, the application of international law or the intervention of third countries in the conflict is minimal, as many consider this to be the case. subject of actions as "tolerable".
Undoubtedly, the gray zone and hybrid threats have become the new military technique of our era due to their effectiveness and simplicity. However, there should be tighter controls to ensure that this subject of such harmful military techniques cease to go unnoticed.
A characteristic aspect of hybrid warfare is the manipulation of communications and the use of propaganda. These actions are managed to sow citizens' distrust in their institutions, as is currently the case in the relationship between China and the United States, weighed down by US statements to the press about the plan presented by Xi Jinping in 2014 on the New Silk Road, and which denote a halt to the Degree distrust and rejection of the Middle Empire.
It is therefore appropriate for States and international institutions to establish "rules of the game" for this subject and thus maintain world order and peace.
A first essay of this text was presented as a paper at the XXVII International Defense Course held in Jaca in October 2019
Bibliography
Carlos Galán. (2018). Hybrid threats: new tools for old aspirations. 2019, from Real Instituto El Cano. Website
Lyle J. Morris, Michael J. Mazarr, Jeffrey W. Hornung, Stephanie Pezard, Anika Binnendijk, Marta Kepe. (2019). Gaining Competitive Advantage in the Grey Zone. 2019, by RAND CORPORATION. Website
Josep Barqués. (2017). Towards a definition of the "Grey Zone" concept. 2019, from Instituto Español de programs of study Strategic. Website
Javier Jordán. (2017). Hybrid Warfare: An Catch-It All Concept. 2019, from the University of Granada. Website
Javier Jordán. (2018). International Conflict in the Grey Zone: A proposal from the perspective of offensive realism. 2019, from Revista Española de Ciencia Política. Website
Javier Jordán. (2019). How to counter hybrid strategies. 2019, from the University of Granada. Website
Guillem Colom Piella. (2019). The Hybrid Threat: Myths, Legends, and Realities. 2019, from Instituto Español de programs of study Strategic. Website
Murat Caliskan. (2019). Hybrid warfare through the lens of strategic theory. 2019, from Defense & Security Analysis, 35:1, 40-58. Website
Rubén Arcos. (2019). EU and NATO confront hybrid threats in centre of excellence. 2019, from Jane's Intelligence Review. Website
Publisher: Geert Cami Senior Fellow: Jamie Shea Programme Manager: Mikaela d'Angelo Programme Assistant: Gerard Huerta publisher: Iiris André, Robert Arenella Design: Elza Lőw. (2018). HYBRID AND TRANSNATIONAL THREATS. 2019, by Friends of Europe. Website
An interview with Seyed Mohammad Marandi, University of Tehran. (2019). Iranians Will Not Forget the Hybrid War Against Iran. 2019, by Comunidad Saker Latinoamérica. Website
[1] This idea became popular among the defense community after the presentation of the essay "Conflict in the 21st Century." Guillem Colom Piella. (2019). The Hybrid Threat: Myths, Legends, and Realities. 2019, from Instituto Español de programs of study Strategic
[2] Reform of terrorism offences through Organic Law 2/2015. group of programs of study in International Security (GESI), University of Granada.
[3] Joint Communication to the European Parliament, committeeto the committee Economic and Social Wuropeo and the committee of the Regions. ̋ European Union Cybersecurity Strategy: An Open, Secure and Secure Cyberspace ̋.
[Sheila A. Smith, Japan Rearmed. The Politics of Military Power. Harvard University Press. Cambridge, 2019. 239 p.]
review / Ignacio Yárnoz
 Japan is currently facing a status of sensitive national security. On the north, the country is constantly subjected to harassment by the Democratic People's Republic of Korea in the form of ballistic missile tests that often land in Japanese territorial waters. To the east and southeast, Japan's sovereignty over its territorial waters, including the disputed Senkaku Islands, is threatened by a China increasingly keen to flex its economic and military muscles.
Japan is currently facing a status of sensitive national security. On the north, the country is constantly subjected to harassment by the Democratic People's Republic of Korea in the form of ballistic missile tests that often land in Japanese territorial waters. To the east and southeast, Japan's sovereignty over its territorial waters, including the disputed Senkaku Islands, is threatened by a China increasingly keen to flex its economic and military muscles.
And as if this were not enough, Japan is already questioning the security that the United States can or wants to provide in the event of a regional conflict. If in the past Japan feared being dragged into a war because of the American predisposition to use fire to solve certain situations, now what Tokyo fears is that the United States will not accompany it when it comes to defending its sovereignty.
That national security dilemma is what Japan Rearmed tackles. The Politics of Military Power, by Sheila A. Smith, a senior fellow at the Council on Foreign Relations in the United States. The book brings together the different views on this issue. The Japanese government's position is that Japan should be more confident in itself in order to maintain its own security. But this is where the biggest hurdle arises. Since its defeat in World War II and subsequent U.S. domination of the country until 1952, the national Armed Forces have been downgraded to "Self-Defense Forces." The reality is that the 1947 Constitution, specifically its article issue 9, continues to limit the functions of Japanese troops.
Introduced directly by the U.S. command, the article 9, never amended, reads: "Sincerely aspiring to an international peace based on justice and order, the Japanese people Withdrawal war as the sovereign right of the nation and the threat or use of force as a means of settling international disputes. (2) In order to carry out the wish expressed in the preceding paragraph, land, sea or air forces and any other military potential shall not be maintained in the future. The right of belligerency of the state shall not be recognized."
This article, a novelty at the time, was intended to open an era safe from warmongering tendencies, in which the project of the United Nations would be the basis for collective security and the peaceful settlement of disputes. However, history itself showed how in a matter of a few years the very architects of that Constitution called for the rearmament of Japan in the context of the Korean War; it was now too late for a rethinking of the foundational limitations of the new Japan.
Following changes in Asia's geopolitics over the past 30 years after the end of the Cold War, Japan has taken steps to regain its international presence, but even today it continues to stumble under the constraint of its constitution. As Smith rightly describes, there are many legal hurdles that the Japan Self-Defense Forces have had to overcome since 1945. Issues such as Japan's performance abroad under the flag of the United Nations, its absence from the 1st Gulf War, the discussion The debate on resilience after an attack by North Korea or Japan's performance in the 2nd Gulf War are all discussed and analyzed in this book. In addition to this, the author tries to explain the reasons and arguments in each of the debates concerning the article 9, such as self-defense, the role of the Self-Defense Forces and the relationship with the United States, issues that confront the Japanese political elite. Several generations of political leaders have tried to resolve the dilemma of guaranteeing Japan's security and interests without limiting the capabilities of its armed forces, although so far there has been no consensus to change certain constitutional budgets, in the direction in which Prime Minister Shinzo Abe is pushing.
Japan rearmed is a 360 review Degrees where the reader finds a complete analysis of the main obstacles faced by the Japan Self-Defense Forces and what their role may be. development future. In a framework More broadly, the book also addresses the role of the Armed Forces in a democracy, which must reconcile its rejection of violence with the obligation to guarantee collective defense.
[Glen E. Howard and Matthew Czekaj (Editors), Russia's military strategy and doctrine. The Jamestown Foundation. Washington DC, 2019. 444 pages]
REVIEW / Angel Martos Sáez
 |
This exemplar acts as an answer and a guide for Western policymakers to the quandary that 21st century Russia is posing in the international arena. Western leaders, after the annexation of Crimea in February-March 2014 and the subsequent invasion of Eastern Ukraine, are struggling to come up with a definition of the aggressive strategy that Vladimir Putin's Russia is carrying out. Non-linear warfare, limited war, or "hybrid warfare" are some of the terms coined to give a name to Russia's operations below the threshold of war.
The work is divided in three sections. The first one focuses on the "geographic vectors of Russia's strategy". The authors here study the six main geographical areas in which a clear pattern has been recognized along Russia's operations: The Middle East, the Black Sea, the Mediterranean Sea, the Arctic, the Far East and the Baltic Sea.
The chapter studying Russia's strategy towards the Middle East is heavily focused on the Syrian Civil War. Russian post-USSR foreign-policymakers have realized how precious political stability in the Levant is for safeguarding their geostrategic interests. Access to warm waters of the Mediterranean or Black Sea through the Turkish straits are of key relevance, as well as securing the Tartus naval base, although to a lesser extent. A brilliant Russian military analyst, Pavel Felgenhauer, famous for his predictions about how Russia would go to war against Georgia for Abkhazia and South Ossetia in 2008, takes us deep into the gist of Putin's will to keep good relations with Bashar al-Assad's regime. Fighting at the same time Islamic terrorism and other Western-supported insurgent militias.
The Black and Mediterranean Seas areas are covered by a retired admiral of the Ukrainian Navy, Ihor Kabanenko. These two regions are merged together in one chapter because gaining access to the Ocean through warm waters is the priority for Russian leaders, be it through their "internal lake" as they like to call the Black Sea, or the Mediterranean alone. The author focuses heavily on the planning that the Federation has followed, starting with the occupation of Crimea to the utilization of area denial weaponry (A2/AD) to restrict access to the areas.
The third chapter concerning the Russia's guideline followed in the Arctic and the Far East is far more pessimistic than the formers. Pavel K. Baev stresses the crucial mistakes that the country has done in militarizing the Northern Sea Route region to monopolize the natural resource exploitation. This tool, however, has worked as a boomerang making it harder for Russia nowadays to make profit around this area. Regarding the Far East and its main threats (North Korea and China), Russia was expected a more mature stance towards these nuclear powers, other than trying to align its interests to theirs and loosing several opportunities of taking economic advantage of their projects.
Swedish defense ministry advisor Jörgen Elfving points out that the BSR (acronym for Baltic Sea Region) is of crucial relevance for Russia. The Federation's strategy is mainly based on the prevention, through all the means possible, of Sweden and Finland joining the North Atlantic Alliance (NATO). Putin has stressed out several times his mistrust on this organization, stating that Western policymakers haven't kept the promise of not extending the Alliance further Eastwards than the former German Democratic Republic's Western border. Although Russia has the military capabilities, another de facto invasion is not likely to be seen in the BSR, not even in the Baltic republics. Instead, public diplomacy campaigns towards shifting foreign public perception of Russia, the funding of Eurosceptic political parties, and most importantly taking advantage of the commercial ties (oil and natural gas) between Scandinavian countries, the Baltic republics and Russia is far more likely (and already happening).
The second section of this book continues with the task of defining precisely and enumerating the non-conventional elements that are used to carry out the strategy and doctrine followed by Russia. Jānis Bērziņš gives body to the "New Generation Warfare" doctrine, according to him a more exact term than "hybrid" warfare. The author stresses out the conscience that Russian leaders have of being the "weak party" in their war with NATO, and how they therefore work on aligning "the minds of the peoples" (the public opinion) to their goals in order to overcome the handicap they have. An "asymmetric warfare" under the threshold of total war is always preferred by them.
Chapters six and seven go deep into the nuclear weaponry that Russia might possess, its history, and how it shapes the country's policy, strategy, and doctrine. There is a reference to the turbulent years in which Gorbachev and Reagan signed several Non-Proliferation Treaties to avoid total destruction, influenced by the MAD doctrine of the time. It also studies the Intermediate-Range Nuclear Forces (IMF) Treaty and how current leaders of both countries (Presidents Trump and Putin) are withdrawing from the treaty amid non-compliance of one another. Event that has sparked past strategic tensions between the two powers.
Russian researcher Sergey Sukhankin gives us an insight on the Federation's use of information security, tracing the current customs and methods back to the Soviet times, since according to him not much has changed in Russian practices. Using data in an unscrupulously malevolent way doesn't suppose a problem for Russian current policymakers, he says. So much so that it is usually hard for "the West" to predict what Russia is going to do next, or what cyberattack it is going to perpetrate.
To conclude, the third section covers the lessons learned and the domestic implications that have followed Russia's adventures in foreign conflicts, such as the one in Ukraine (mainly in Donbas) and in Syria. The involvement in each one is different since the parties which the Kremlin supported are opposed in essence: Moscow fought for subversion in Eastern Ukraine but for governmental stability in Syria. Russian military expert Roger N. McDermott and analyst Dima Adamsky give us a brief synthesis of what experiences Russian policymakers have gained after these events in Chapters nine and eleven.
The last chapter wraps up all the research talking about the concept of mass mobilization and how it has returned to the Federation's politics, both domestically and in the foreign arena. Although we don't exactly know if the majority of the national people supports this stance, it is clear that this country is showing the world that it is ready for war in this 21st century. And this guide is here to be a reference for US and NATO defense strategists, to help overcome the military and security challenges that the Russian Federation is posing to the international community.
Some U.S. and Canadian diplomats who were in Havana between 2016 and 2018 are still not fully recovered from ailments they suffered
![U.S. Embassy building in Cuba [department de Estado] [ de Estado] U.S. Embassy building in Cuba [department de Estado] [ de Estado]](/documents/10174/16849987/ataques-sonicos-blog.jpg)
▲ Building of the U.S. Embassy in Cuba [department de Estado].
ANALYSIS / Eduardo Villa Corta
Three years ago, staff U.S. diplomats stationed in Cuba began to feel physical discomfort supposedly caused by strange sounds to which they had apparently been exposed; Washington spoke of a "sonic attack. However, although the symptoms suffered by those affected have been determined to be anomalous, it has not been possible to establish what caused them. Was it really an attack? Who was behind it? We review here the main hypotheses and conjectures that have been made, and point out their weaknesses.
In late 2016 and early 2017, several U.S. diplomats stationed in Havana, as well as members of their families, reported suffering from dizziness, vertigo and sharp pains in their ears that could be caused by strange sounds to which they had been exposed. According to their testimonies, the sounds came from a specific direction, and they had heard them in their own residences or, in some cases, in hotel rooms, while people staying in neighboring houses or adjoining rooms had not heard any special sounds. The phenomenon also affected Canadian diplomats in the Cuban capital. In all, some forty people were treated for these symptoms.
Acoustic attack
Echoing the facts reported by its staff in Cuba, in mid-2017 the U.S. State department stated that the symptoms could have been caused by a sonic attack by the Cuban government directed against diplomats and their families. In October 2017, President Donald Trump directly accused Havana: "I believe Cuba is manager; yes, I do."
At the beginning of 2018 the department of State issued a statement alert not to travel to Cuba due to a possible health crisis and withdrew a good part of the staff of the mission statement diplomatic in Havana, reducing the activity of this to the minimum possible. At that time, a total of 24 Americans had been affected.
At the time, the Canadian government also indicated that its diplomats had experienced similar discomfort. Ottawa decided to evacuate the families of its employees in Cuba and in early 2019 proceeded to reduce the staff of the embassy in the face of what appeared to be the appearance of a fourteenth case.
The Cuban government denied from the outset being involved in any harassment operation against the U.S. or Canada. ˝There is no test about the cause of the reported ailments, nor is there any evidence to suggest that these health problems have been caused by an attack of any kind˝, Havana assured. Raul Castro's government offered its cooperation in the research of the facts, with nothing coming to light that could explain the case. No devices that could have provoked the sounds appeared.
Adding confusion to the status, at least two US diplomats stationed in China, busy at the consulate general in Guangzhou, the largest that the US has in the country, presented in early 2018 also the symptoms already described. Washington evacuated them and issued a health warning about missions in mainland China.
The Associated Press published in October 2017 a recording of the alleged sounds causing the reported ailment, and indicated that government agencies had been unable to determine the nature of the noise and explain its relationship to the bodily disorders caused. Months later, he noted that internal FBI reports did not even establish that there had been an "attack". Other media highlighted the poor cooperation in the research, due to jurisdictional zeal, between the department of State, the FBI and the CIA.
Symptoms of "Havana syndrome".
A medical team from the University of Pennsylvania, at the request of the U.S. Government, examined 21 people affected by what the press began to call "Havana syndrome". The research, initially published in March 2018 in the Journal of the American Medical Association (JAMA), indicated that most of the patients reported problems with report, concentration, and balance, and determined that they appeared to have suffered injuries to extensive brain networks.
data Further MRI scans of the same team extended to 40 patients, released in July 2019, led to the conclusion that the diplomats had experienced some craniocerebral trauma. The results of the MRI scans, compared with those of a group of healthy people, showed differences in the volume of the white and gray substances of the brain, in the integrity of the cerebellar microstructures and in the functional connectivity of the subnetworks for hearing and spatial vision, but not for executive functions.
This report concluded that the staff diplomat had been physically injured, although it could not determine the cause. He also noted that patients do not experience a usual recovery, as they are not recovering quickly from symptoms, as is the case in other cases of similar "concussions" or ear problems.
IF IT WASN'T AN ATTACK, WHAT WAS IT?
As no clear cause has been established as to what caused the ailments suffered by the US and Canadian diplomatic staff and some members of their families, the very reality of an attack has been called into question. Although various alternative explanations have been put forward, none of them are fully convincing.
1) Collective hysteria
Formulation. Some neurologists and sociologists, such as Robert Bartholomew, have suggested that it could be a case of mass hysteria. Given the pressure to which some of the diplomats working in very unfriendly environments are subjected, and the endogamic relationship in which they live, living almost exclusively among themselves, it could explain a mutual conviction of an external attack that even has somatic consequences.
Weak spot. Both the research of the University of Pennsylvania and the doctor of the department of State, Charles Rosenfarb, who appeared before the committee of Foreign Relations of the Senate, came to rule out that the symptoms suffered by the diplomats were due to a mere mental mechanism. It is very difficult that about sixty people, including Americans and Canadians, convinced each other of an aggression of this kind subject and then almost all of them developed the same brain lesions.
2) Microwave
Formulation. The researcher team at the University of Pennsylvania, while not pointing to any possible cause of the ailments, did not rule out certain assumptions, such as that of microwave affectation. This aspect was insisted upon by a research published in 2018 in the journal Neural Computation, which considered the symptoms consistent with exhibition to electromagnetic microwave (RF/MW) radiation.
Weak point. Not all the symptoms shown by patients could be a consequence of the exhibition of such a radiation subject, which also has a diverging literature on its effects on the human body. In addition, there is no known microwave weapon that can affect the brain.
3) Ultrasound
Formulation. A team of computer experts at the University of Michigan suggested in 2018 that it could be a case of exhibition to some subject ultrasound, perhaps coming from malfunctioning listening equipment mixing multiple ultrasonic signals.
Weak point. The recording of one of the sound episodes - the sample broadcast by AP - is not sufficient to be able to determine its nature. It is also possible that the sound was somewhat different in other cases.
4) Crickets
Formulation. A research from the Universities of California-Berkeley and Lincoln, from the existing sound sample , considered in January 2019 that the possible cause of the attacks was made by cricketsThe study, specifically crickets Anurogryllus muticus. The research was a comparative study between the sound emitted by that variant of crickets and the sample of one of the Havana acoustic episodes.
Weak point. The sound perceived by the diplomats was directional, so it was not heard by neighboring people. If they had been crickets in their natural environment, the sound would have spread around.
5) Neurotoxins
Formulation. A joint study by two Canadian research centers in May 2019 attributed the symptoms suffered by diplomats to exhibition to neurotoxins from pesticides used to spray mosquitoes, a internship common occurrence in embassy buildings.
Weak point. The diplomats affected related the beginning of their physical discomfort to situations experienced in their own residences or in hotel rooms, where there was no fumigation.
IF IT WAS AN ATTACK, WHO DID IT?
Given that the previous explanations do not seem entirely solid, the US Government maintains the hypothesis of an attack. If it really happened, who was behind it? Here, too, there are various conjectures.
1) Castro regime
The first option considered, assumed in principle by the US given the public accusations made from Washington, has been to attribute the alleged attacks to the Cuban regime itself. With them, Havana would try to maintain pressure on the Americans, in spite of the formal reestablishment of diplomatic relations, with the goal to mark each other's territory.
Weak point. The incidents began to occur during the Obama Administration, in a context of a ˝honeymoon˝ marked by the reopening of embassies and the visit of Barack Obama to Havana. The normal thing is that at the end of 2016, in view of the U.S. elections, the Castro regime would not want to give reasons to the next U.S. president to twist the diplomatic line opened by Obama. It could make sense that after Donald Tump's later revocation of the previous openness measures, Cuba would want to punish the new Administration, but not before seeing the direction it would take; in any case, the attacks would only justify the hard line followed by Trump, which does not benefit the island.
2) A sector of Castroism
Fidel Castro was attributed with an unaccommodating attitude towards his brother Raul's decision to reestablish diplomatic relations with the United States. Although he died in November 2016, people around him might have tried to torpedo that rapprochement, convinced that hostility with Washington was the best way to ensure the survival of the regime as conceived by its founder.
Weak point. Although Fidel Castro's reluctance towards rapprochement with the U.S. is true, it is difficult to think that the most conservative sector within Castroism would dare to boycott so directly Raul Castro's fundamental political line. It is another thing that, after he handed over the presidency of Cuba to Miguel Díaz-Canel in April 2018, some sectors within the regime could make internal movements to send certain messages, but the changeover occurred when most of the acoustic episodes had already taken place.
3) A third country (Russia, China)
The third option would be that a third country generated the attacks. American intelligence indicates that the most viable option in this case would be Russia. Moscow has been keen to return to operating in the Caribbean, as in the Cold War, and aggression against U.S. diplomats in Cuba would fit in with its strategy. It has also been suggested that China might want to repay Washington in its backyard with the same harassment that the Chinese believe they feel from the US in their nearest seas.
Weak point. The return of Russia to the Caribbean is certainly documented, and it is conceivable that Moscow could have promoted a punctual action against some specific goal , but it seems difficult that it would have sustained over time an operation that harms Cuba's sovereignty. As for China's presence in the US neighborhood, it is a less confrontational move than the one carried out by Russia. Moreover, if Beijing had chosen foreign soil in order to better erase the traces of an action against US diplomats, then the cases recorded in Guangzhou would not have occurred.
[Hebert Lin & Amy Zegart, eds. Bytes, Bombs, and Spies. The strategic dimensions of offensive cyber operations. The Brookings Institution. Washington, 2019. 438 p. ] REVIEW / Albert Vidal
review / Pablo Arbuniés
 Just as in the second half of the 20th century the world experienced the degree program nuclear weapons between the US and the USSR for world hegemony, everything seems to indicate that the degree program that will mark the 21st century is that of cyberspace. Ever since the department The inclusion of cyberspace as the fifth domain of the country's military operations (along with land, sea, air, and space) has made clear the paramount importance of its role in global security.
Just as in the second half of the 20th century the world experienced the degree program nuclear weapons between the US and the USSR for world hegemony, everything seems to indicate that the degree program that will mark the 21st century is that of cyberspace. Ever since the department The inclusion of cyberspace as the fifth domain of the country's military operations (along with land, sea, air, and space) has made clear the paramount importance of its role in global security.
However, the very nature of cyberspace makes it a completely different field from what we might call kinetic security fields. The only constant in cyberspace is change, so any study and strategic approach must be able to adapt quickly to changing conditions without losing efficiency and maintaining enormous precision. This is a real challenge for all actors operating in cyberspace, both national and private. At the national level, the incorporation of cyber operations into the U.S. national security strategy (NSS) and the development of a cyberwarfare doctrine by the department are the two main pillars on which the new degree program through cyberspace.
"Bytes, Bombs, and Spies" explores the big questions posed by this new challenge, presenting very different approaches to different situations. Probably the greatest value offered by the book is precisely the different ways of dealing with the same problem defended by the more than twenty authors who have participated in its elaboration, coordinated by Herbert Lin and Amy Zegart. These authors collaborate in the 15 essays that make up the book. They do it with the idea of turning a topic as complex as offensive cyber operations into something achievable for non-expert readers. topic, but without sacrificing the depth and detail of an academic work.
Throughout the volume, the authors not only propose what the approach of the framework theoretical. They also assess the U.S. government's policies in the field of offensive cyber operations and propose what the points should be core topic in the development of new policies and adaptation of previous ones to the changing cyber environment.
The book tries to answer the big questions asked about cyberspace. From the use of offensive cyber operations in a framework from conflict to the role of the private sector, through the escalation dynamics and the role of deterrence in cyberspace or the intelligence capabilities needed to carry out effective cyber operations.
One of the main issues is how cyber operations are included in the framework of the dynamics of a scale of conflict. Is it permissible to respond to a cyberattack with kinetic force? And with nuclear weapons? The U.S. government's current cyber-doctrine leaves both doors open, facing a response based on the effects of the attack over the means. This idea is described as incomplete by Henry Farrell and Charles L. Glaser in their chapter, in which they argue for the need to take into account more factors, such as the perception of the threat and attack by other actors, as well as public opinion and the international community.
Continuing with the theoretical approaches, the main question raised by this book is whether it is sensible to apply the same principles in the strategic study of cyberspace that were applied to nuclear weapons during the cold war to answer the questions posed above. And since this is a relatively new field in which global hegemony and stability can be at stake from the outset, how this question is answered can mean the difference between stability or absolute chaos.
This is precisely what David Aucsmith proposes in his chapter. In it, he argues that cyberspace is so different from classical strategic disciplines that its strategic dimensions must be rethought from scratch. The disintermediation of governments, incapable of encompassing all of cyberspace, opens up a niche for private companies specializing in cybersecurity, but even these will not be able to completely fill what the government does in other domains. For his part, Lucas Kello tries to fill the sovereignty gap in cyberspace with the aforementioned private participation, proposing the convergence between governments and citizens (through the private sector) in cyberspace.
In conclusion, "Bytes, Bombs, and Spies" tries to answer all the main questions posed by cyberspace, without being unattainable to an audience that is not an expert in cyberspace. topic, but maintaining rigor, precision, and depth in its analysis. .
Showing the range 41 - 50 of 95 results.
